Cybersecurity is one of the most prominent risk factors for commercial companies, government agencies, and individual users of systems and services1. This is partly because cybersecurity faces multiple risk vectors such as insider threats, data spills, ransomware, hacking, supply chain risks, and human error. The potential consequences of such risks can be catastrophic, ranging from identity theft, privacy violations, revenue loss, and even violation of federal law.
To combat this, organizations rely upon many processes and tools to identify, track, and mitigate these risks across the technical and compliance landscapes. This article focuses on compliance: specifically, the National Institute of Standards & Technology (NIST) Risk Management Framework (RMF)2 and the Assessment & Authorization (A&A) process. Originally the RMF was designed for federal agencies, but private sector companies commonly use it to improve their security hygiene.
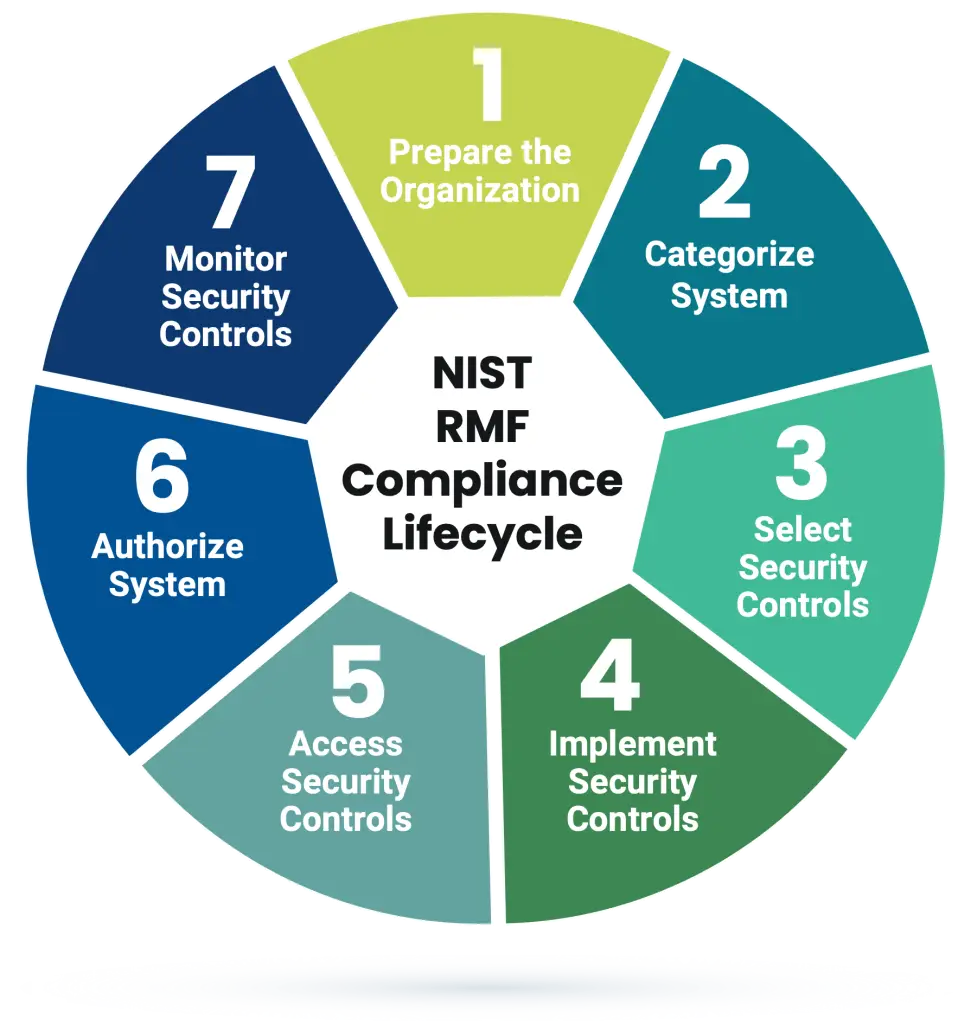
The RMF focuses on managing versus eliminating risk, which is accomplished through the RMF’s seven steps to formally track an asset through the accreditation process and eventually approve the asset to operate, in what is called an Authorization to Operate (ATO).
While the process may appear simplistic, when adopted by different organizations with different missions, lines of business, types of data, and cybersecurity acumen, this framework can become convoluted, bloated, ineffective, and dangerous. This is especially true when project teams view the process as just “paperwork” or lack the security forethought needed to get their product to production with an ATO.
In cybersecurity, there are varying opinions on how to get to ATO “fast.” In a rapidly changing cyber environment, time is of the essence. But focusing on the speed of the process raises the question of whether the quality—and therefore effectiveness—will be reduced.
CASE STUDY
The root of most ATO-related challenges for our customers stems from the lack of communication between security teams and the rushed nature of planning periods.
Often, the length of the ATO process is an afterthought in early development, with timelines not accounting for the near yearlong queues from project start to the granting of ATO certification for a system. By this point, requirements may have changed, iterations may have taken place, and even some projects scrapped by frustrated clients who were not anticipating the wait time.
Rigorous planning is key to achieving accreditation, as evidenced by our ATO approach supporting a defense customer. Before development work even started, our team set aside eight months of planning time focused on the ATO process.
Within that timeframe, the team created a static production environment and ensured no changes were made. This allowed the team to coordinate with all the ATO stakeholders while providing the resources to work on all the documentation required for the ATO package. By the end of the 8-month period, we were awarded ATO and had an established RMF process throughout the life of the accreditation, highlighting the importance of not cutting corners in the planning and review preparation process.
With extensive experience in private and public sectors, NT Concepts has put together the following series of generalized recommendations to improve both the timeliness and quality of our customers’ compliance processes.
First, we address what organizations can implement at the senior-leadership level to enable efficiency, shore up fundamentals, and build trust between our security bodies and project teams. Following that, we supply recommendations for project teams that aid in building security during development, generating precise, complete documentation, and being the boots on the ground reporting upward to senior leadership.
Senior leadership cannot create secure systems on their own. It takes the entire organization working together in a symphony to manage organizational risk.
No one can whistle a symphony;
it takes an orchestra to play it”.
- H.E. Luccock
Organization To-Dos
Common Control Providers
One initiative that significantly impacts the efficiency and quality of accreditations is the identification and authorization of Common Control Providers (CCPs). CCPs are typically enterprise systems or services used by subordinate systems, applications, or services. CCPs get their name because they handle the implementation and configuration of security control requirements which their customers then inherit.
Organizations must identify and accredit their CCPs before any other system or service and revisit and re-validate their authorizations continuously. CCPs are the backbone of an organization’s ATO and are fundamental to the successful and secure continuation of mission operations.
Imagine that every time you used a credit card, you were asked to provide proof that:
- the card is yours,
- you have an online account with the provider,
- the provider is the actual issuer of the card,
- the provider employs security measures to protect against theft, and
- the provider will pay the business even if you are unable to pay the credit card bill?
You would be frustrated that you are being put in the position of proving something that is the provider’s responsibility.
Now translate that over into security controls and the accreditation process. Say your organization requires all applications to use enterprise public key infrastructure (PKI), and there are ten security controls that relate to the implementation and configuration of PKI.
Your organization has 2,000 unique accreditation records (including applications, systems, and services) required to answer those ten controls. A CCP is not identified and accredited, and those ten controls are not made available to be inherited by the other 1,999 records. You now have project teams and assessors spending time continuously answering and verifying 19,990 PKI security controls, versus an assessor performing the assessment once initially and then with periodic verification.
Now start to calculate the hours spent on work that neither the project team nor the assessor can prove or verify. CCPs not only add value and improve your security posture, but significantly reduce time and effort across your entire organization.
Communication
At the heart of our organizational approach is consistent and meaningful communication. Communicate early and often, ensuring the correct audience is reached. If you have a communications team or office, make certain they are in the loop on all compliance-related meetings, discussions, boards, or decision-making.
Where possible, allow the workforce at large to attend non-sensitive meetings about compliance issues for full transparency about the process and decision-making. As you and your project teams start to trust each other and work more closely together, communication will happen more organically. Watch for feedback from project teams that reference them not being aware of changes or decisions, and make sure the corresponding office is aware and the course corrects accordingly.
Experienced (and qualified!) subject matter experts
Cybersecurity presents an interesting challenge when gathering subject matter experts (SMEs). The topic itself has a low bar to entry, meaning there is an abundance of experts on the topic, but they may not be qualified in the specific domains required by your project. Further complicating the vetting of SMEs is the lack of cybersecurity expertise in the market to fill critical positions3, as well as open policy or governance slots. Organizations can miss the mark in generating position descriptions or hiring the correct personnel. Vague or misleading position requisitions can lead to mismatched roles and personnel, resulting in high turnover rates (increasing the anxiety over getting someone into the position) or worse, a disgruntled or unmotivated employee.
Organizations should use vetted and experienced employees or a third party to generate and review position requisitions against requirements. Personnel should not have a financial stake in successfully hiring or retaining an employee for the position(s). The outcome should be that you have the correct skillset matched to the job, and you are not paying for a senior-level expert where a junior-level would suffice. Make it a priority to staff full-time SMEs that can be called upon for their trusted ability in cyber security as needed, saving time and money overall while cultivating a full-time culture of excellence in the field.
Reduce redundant systems and services
The leaner you run your network, system, and services, the easier it will be to perform critical data management and meet security requirements. Does your organization have four data lakes with the same data in each? That may be an area where you could consolidate them down to one. Do you have two to three ticketing services in use across the organization? Consolidate them.
A&A-specific recommendations
Develop an A&A knowledge base
Where do new project team members find security controls with Organization-Defined Values (ODVs)? Where do they become educated on criticality and availability requirements? How do they find points of contact for assessors, Information System Security Managers (ISSM), or other A&A personnel? Where do they find documentation of acronyms or nomenclature specific to the A&A process?
Your organization should have an established knowledge base that encompasses anything a project team, project manager, information systems Security Engineer (ISSE), or ISSM would need to successfully prepare for the A&A process. If project teams must guess, rely on word-of-mouth, or fall back on how they did it in their last job, you may indirectly cause delay and inaccuracy, which is costly and poses a security risk. An expansive and up-to-date knowledge base will also greatly improve your overall communication with the workforce.
Develop Authoritative Templates
Develop organization-specific templates for critical documentation (such as Contingency Plans, Incident Response Plans, Configuration Management Plans, and Roles and Responsibilities Matrixes) and enforce their use. Ensure the contents of the documents include your organization’s identified security control requirements so project teams can create one document that potentially answers several to a dozen security controls, and that they can update without having to also update specific security control responses. This type of document allows project teams to “kill two birds with one stone,” in that it answers both security controls AND provides a supporting artifact in a singular reference.
Criticism may not be agreeable, but it is necessary. It fulfills the same function as pain in the human body. It calls attention to an unhealthy state of things.
- Winston Churchill
Encourage constant feedback
Organizations should continuously welcome and encourage feedback from employees and customers to motivate their workforce and realize the entire value spent on expertise. Security is a “dirty word” in many organizations, typically caused by the perception of security considerations being the “bad cop” who only says no and enjoys the power trip of decision-making.
Help change that perception by being genuinely interested and eager to hear feedback regarding security. Establish a transparent, repeatable process for collecting feedback, reviewing it, and providing a response that explains the decisions. If financially solvent, have monetary incentives for suggestions that improve your security posture. Overall, this will cost your organization significantly less than a data breach, which averages $9.44M4 in the United States.
References
1 Jensen, R. (2022, September 7). Business leaders rank cybersecurity as most serious risk facing their company. Security Today. Retrieved November 16, 2022, from https://securitytoday.com/articles/2022/09/07/business-leaders-rank-cybersecurity-as-most-serious-risk-facing-their-company.aspx
2 Information Technology Laboratory, Computer Security Division. (2016, November 30). About the RMF – NIST risk management framework: CSRC. NIST CSRC. Retrieved November 16, 2022, from https://csrc.nist.gov/projects/risk-management/about-rmf
3 Lake, S. (2022, June 30). Companies are Desperate for Cybersecurity Workers. Fortune. Retrieved November 16, 2022, from https://fortune.com/education/business/articles/2022/06/30/companies-are-desperate-for-cybersecurity-workers-more-than-700k-positions-need-to-be-filled/
4 IBM. (n.d.). Cost of a Data Breach 2022: A million-dollar race to detect and respond. IBM. Retrieved November 16, 2022, from https://www.ibm.com/in-en/security/data-breach
5 Biden, J. R. (2021, May 12). Executive Order on Improving the Nation’s Cybersecurity. The White House. Retrieved November 16, 2022, from https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/
6 Biden, J. R. (2022, January 19). Memorandum on improving the Cybersecurity of National Security, Department of Defense, and Intelligence Community Systems. The White House. Retrieved November 16, 2022, from https://www.whitehouse.gov/briefing-room/presidential-actions/2022/01/19/memorandum-on-improving-the-cybersecurity-of-national-security-department-of-defense-and-intelligence-community-systems/